This setting manages how user access to the FVTerm application is secured within the Internet Information Server (IIS) environment.
Note that in some environments other security frameworks may be utilized to identify users and manage access in a way that is outside the scope of this setting. For these environments leave the default set (Macro User Detection).
Value |
Description |
Integrated Windows Security / Active Directory |
A user will need to be signed-in as a Windows User or will get a pop-up requesting his or her Windows UserID and Password in order to access the terminal emulation.
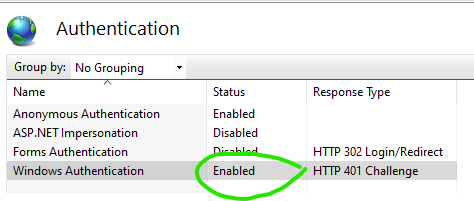
IIS AUTHENTICATION-Windows Authentication MUST BE ENABLED for Web Site in IIS Manager! The Inventu Viewer Installer does not enable this automatically...
|
Google User Authentication |
Select if your organization has a Google Managed account and your users are all members of the managed account.
Requires Server Logging and API Feature.
For details on the steps a Google Domain Administrator takes to enable this option, see https://software.inventu.com/help/html/googAuth
Additional settings when this option is selected include Google Client ID Credentials JSON File, Google Field for Session Identity, Google Admin SDK Credentials JSON File and Google Administrator's Email Account |
SAML 2.0 User Authorization |
SAML 2.0 is used by multiple providers, including SalesForce.com, OKTA Auth0 and Active Directory Federation Services.
See SAML 2.0 General Configuration Notes for important information related to creating a SAML 2.0 application with your SAML 2.0 Provider.
Additional settings when this option is selected include: SAML 2.0 Issuer URL for Authenticating, SAML 2.0 Issuer Identifier, SAML 2.0 Provider Name and SAML 2.0 Certificate File Path
Requires Server Logging and API Feature. |
OAuth2 OpenID Connect User Authorization |
Oauth2 OpenID Connect is very popular and is supported by most IAM providers including AzureAD, Okta, Auth0 and SalesForce. If you have AzureAD, this option is recommended so that you can integrate Groups security.
Additional settings when this option is selected include: OpenID Connect Provider Name, OpenID Connect Issuer URL for Authenticating, OpenID Connect ClientID, OpenID Connect Client Secret, OpenID Connect Claim/Attribute Used for Session Identity, OpenID Connect Authorization Endpoint, OpenID Connect Token Endpoint and OpenID Connect Scope List
Requires Server Logging and API Feature. |
Azure Active Directory (WS Federation) |
Using the AzureAD option is no longer recommended. With the introduction of the OAuth2 OpenID Connect support in 2022, OAuth2 OpenID Connect is the preferred identity option when the provider is AzureAD.
This is because the original AzureAD implementation used WS-Federation--the configuration is more complicated.
Security Groups used to control access to Views, Profiles and Macros are only available with OpenID Connect using Microsoft Graph Groups option.
Only select this if your organization has an Azure Active Directory subscription and you already have been using this option on another server, otherwise, go with Oauth2 OpenID Connect for AzureAD.
Requires Server Logging and API Feature.
For details on the steps an Azure AD Administrator takes to enable this option, see https://software.inventu.com/help/html/FVAZADConfig |
Macro User Detection (default) |
IIS will not require a sign-in but normal host signon security will be required. If the FVTermParent javascript API is not used to start the session, or a Logging Extension Assembly is not used to pull the user identify from the initial HTTP request, there are a number of settings that can provide dynamic capture of the user's mainframe / system identify.
This option cannot be used for Identity with Concurrent User-Based Licensing or controlling access to Views or Profiles, as the user is only identified after signing-in. It is only useful for controlling Macro access as well as having the user's mainframe userid visible in the Admin or Microsoft Management Console. |